Check the TLS versions you are using

Reverse Proxies are playing an important role in those systems that are built using micro-services architectures, since they are used to implement many features as load balancing, compression, caching and, specially, security.
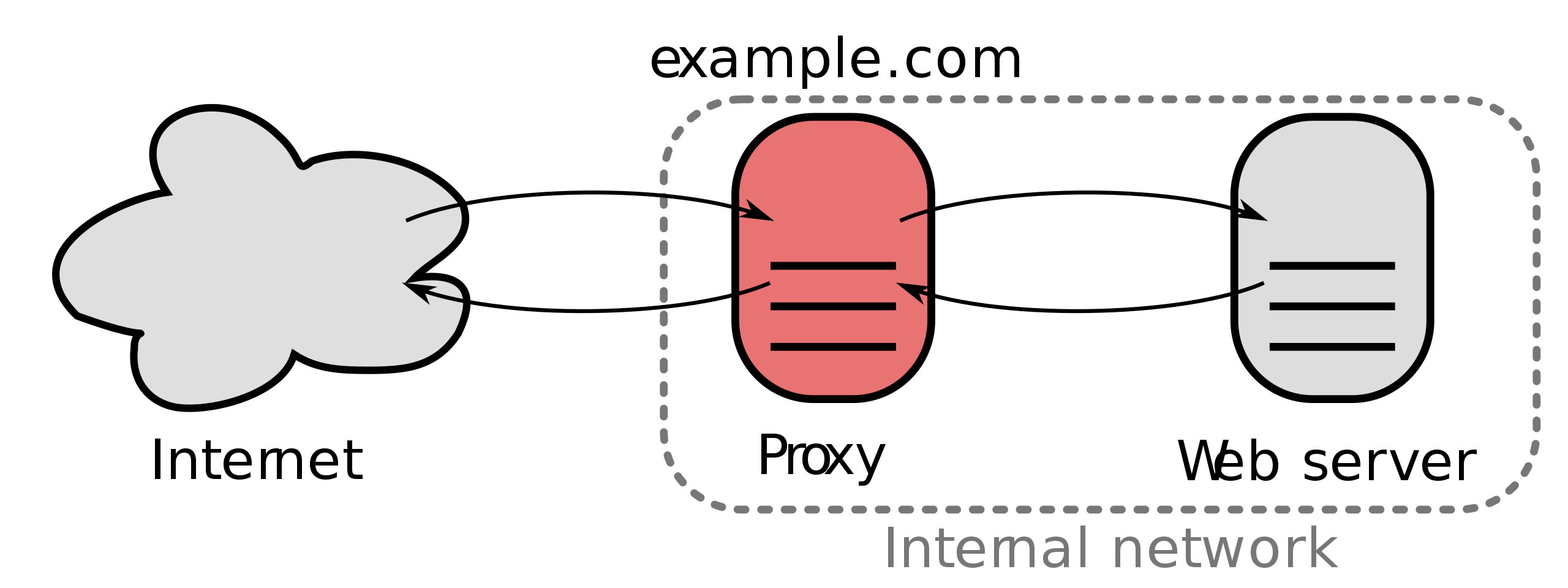
When it comes to securing HTTP traffic using HTTPS [2], it is quite common to use the default configuration files provided or recommended by the vendors [3], but it is important to note that not all TLS protocols versions are enough secure; only the TLSv1.2 and TLSv1.3 versions.
Let’s look at the recommended default protocols. The following is the current default one in [3]:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
but we can even find older versions on the internet like this one:
ssl_protocols SSLv2 SSLv3 TLSv1 TLSv1.1 TLSv1.2;
The following are the main reasons to not use other versions than TLSv1.2 and TLSv1.3:
- SSLv2: it was deprecated in 2011 by RFC 6176
- SSLv3: it was found vulnerable to the POODLE [4] attack that affects all block ciphers.
- TLSv1: it was supposed to be deprecated in March 2020, but more it is more important to note that its implementation allow to downgrade to SSLv3 so it security can be compromised. Since June 30, 2018 it is recommended then to migrate to TLSv1.
- TLSv1.1:: it has solved major security holes that TLSv1 had, but it is not secure enough.
The adoption of the most up to date protocol versions takes time, this SSL Pulse[5] continuous dashboard shows how it is evolving over time.